Create Queue manager
1. Create the queue manager named 'QMSSL' by issuing the following command:
2. Start queue manager
3. Queue manager listener and channel setting.
To automatically start the IBM MQ listener with the queue manager, disable connection auth, use the following MQSC command:
mqsiuid@ftmaixt1:/home/mqsiuid>runmqsc QMSSL
5724-H72 (C) Copyright IBM Corp. 1994, 2015.
Starting MQSC for queue manager QMSSL.
ALTER LISTENER(SYSTEM.DEFAULT.LISTENER.TCP) TRPTYPE(TCP) PORT(1416) CONTROL(QMGR)
1 : ALTER LISTENER(SYSTEM.DEFAULT.LISTENER.TCP) TRPTYPE(TCP) PORT(1416) CONTROL(QMGR)
AMQ8623: WebSphere MQ listener changed.
ALTER QMGR CHLAUTH(DISABLED)
2 : ALTER QMGR CHLAUTH(DISABLED)
AMQ8005: WebSphere MQ queue manager changed.
ALTER QMGR CONNAUTH(' ')
3 : ALTER QMGR CONNAUTH(' ')
AMQ8005: WebSphere MQ queue manager changed.
refresh security
4 : refresh security
AMQ8560: WebSphere MQ security cache refreshed.
define channel(SYSTEM.ADMIN.SVRCONN) chltype(SVRCONN) REPLACE
5 : define channel(SYSTEM.ADMIN.SVRCONN) chltype(SVRCONN) REPLACE
AMQ8014: WebSphere MQ channel created.
end
6 : end
6 MQSC commands read.
No commands have a syntax error.
All valid MQSC commands were processed.
After these step, you can connect to remote queue manager QMSSL via SYSTEM.ADMIN.SVRCONN channel by MQ Explorer.
Keystore creation and SSL setting on MQ Server side
The certificate are stored in /var/mqm/qmgrs/[qmgr_name]
In order to use ikeycmd, export the PATH with the path where ikeycmd command exist:
mqsiuid@ftmaixt1:/var/mqm/qmgrs/QMSSL/ssl>export PATH=/usr/mqm/java/jre64/jre/bin:$PATH
1. Create QM key store
ikeycmd -keydb -create -db /var/mqm/qmgrs/QMSSL/ssl/qmssl.kdb -pw pwd123 -type cms -expire 365 -stash
2. Create CA store
ikeycmd -keydb -create -db /var/mqm/qmgrs/QMSSL/ssl/wmqca.kdb -pw pwd123 -type cms -expire 365 -stash
3. Create CA certificate
ikeycmd -cert -create -db /var/mqm/qmgrs/QMSSL/ssl/wmqca.kdb -pw pwd123 -label wmqssl -dn "CN=QMSSL" -expire 365
4. Extract CA certificate
ikeycmd -cert -extract -db /var/mqm/qmgrs/QMSSL/ssl/wmqca.kdb -pw pwd123 -label wmqssl -target /var/mqm/qmgrs/QMSSL/ssl/wmqca.crt -format ascii
5. Add CA certificate on QM key store
ikeycmd -cert -add -db /var/mqm/qmgrs/QMSSL/ssl/qmssl.kdb -pw pwd123 -label wmqssl -file /var/mqm/qmgrs/QMSSL/ssl/wmqca.crt -format ascii
6. Create certificate request
ikeycmd -certreq -create -db /var/mqm/qmgrs/QMSSL/ssl/qmssl.kdb -pw pwd123 -label ibmwebspheremqqmssl -dn "CN=QMSSL" -file /var/mqm/qmgrs/QMSSL/ssl/qmssl_req.arm
Note: the label name should be ibmwebspheremq+lowercasequeuemanagername.
7. CA sign the certificate
ikeycmd -cert -sign -file qmssl_req.arm -db /var/mqm/qmgrs/QMSSL/ssl/wmqca.kdb -pw pwd123 -label wmqssl -target /var/mqm/qmgrs/QMSSL/ssl/QMSSLcert1.arm -format ascii -expire 365
8. Receive the certificate on QM key store
ikeycmd -cert -receive -db /var/mqm/qmgrs/QMSSL/ssl/qmssl.kdb -pw pwd123 -file /var/mqm/qmgrs/QMSSL/ssl/QMSSLcert1.arm -format ascii
9. Run MQSC command to adapt the queue manager and channel setting.
(1) Changing the key repository location for a queue manager
ALTER QMGR SSLKEYR('/var/mqm/qmgrs/QMSSL/ssl/qmssl');
Note: the stem name 'qmssl' is the QM key store name without file extension .kdb
(2) Define the server connection channel with SSL Cipher Specification (SSLCIPH) by MQSC command
DEFINE CHANNEL('TEST.SSL.SVRCONN') CHLTYPE(SVRCONN) SSLCIPH('TLS_RSA_WITH_AES_128_CBC_SHA256') SSLCAUTH(OPTIONAL);
Keystore creation on MQ Explorer side (client)
You can either create key store on server or local side.
If you created key store on the server, download the client.jks to the local machine.
1. Create key store for explorer
ikeycmd -keydb -create -db client.jks -pw pwd123 -type jks
2. Add CA certificate to key db.
ikeycmd -cert -add -db client.jks -pw pwd123 -label wmqssl -file /var/mqm/qmgrs/QMSSL/ssl/wmqca.crt -format ascii
Connect to MQ server by MQ Explorer
1. Add Remote Queue Manager
2. Enter the Queue manager name, and click Next.
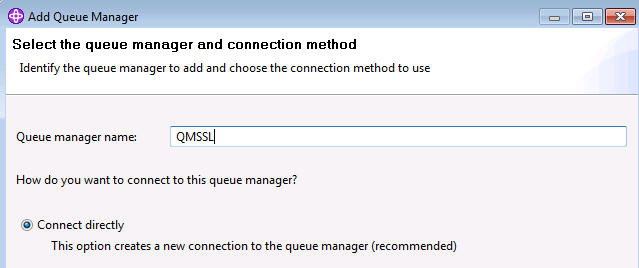
3. Enter the connection details, and click Next.
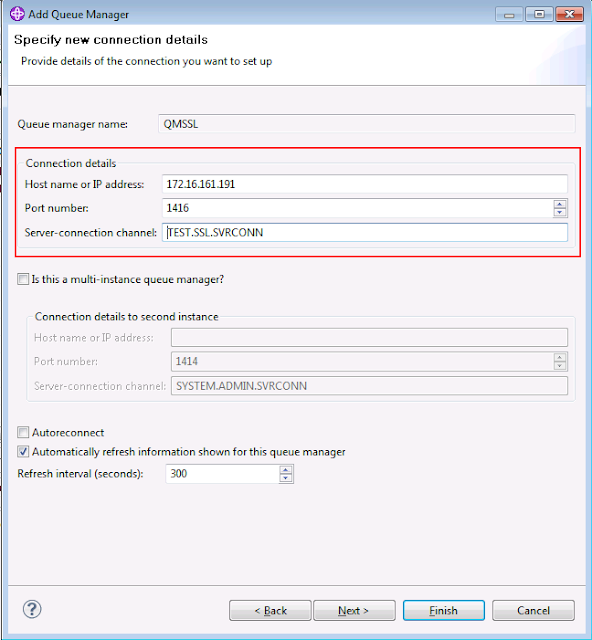
4. Select the key store for the client, and enter password. And click Next.
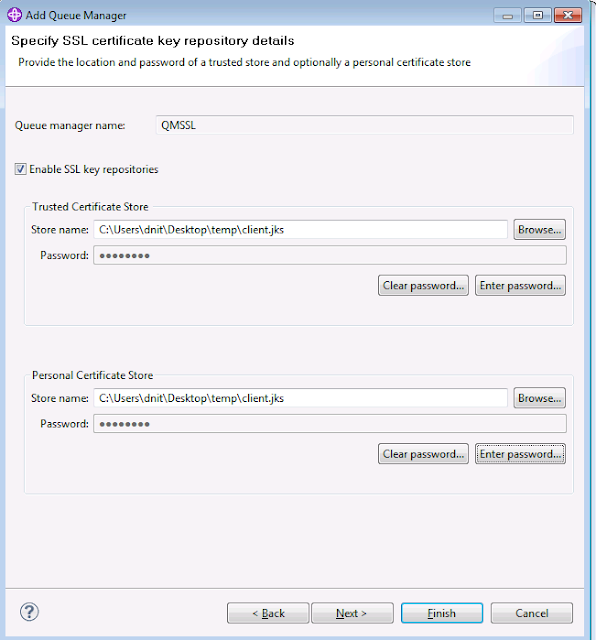


I had done this and get fail.Can you help me?
ReplyDeleteCan you describe in more detail the client part
ReplyDelete